5 Cyber Security Threats to Know
Through the years, cyber attacks have evolved from non-malicious pranks into large-scale criminal operations. While early attacks required specialized technical skills and resources, today’s cyber criminals hack with limited coding skills or knowledge of security systems. Today we’re sharing five cyber security threats you should be familiar with in 2019.
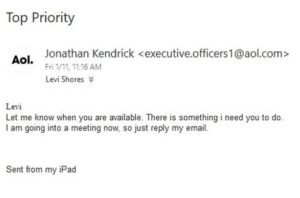
At Digital Technology Partners, we have a multifaceted approach to ensure the security of our clients and their data. In addition to our knowledge of the latest cyber threats, we implement the right hardware and software to ensure the protection of your assets. We’re also experienced in secure wireless networking, encryption, remote access, mobile device management, and user training to ensure you’re protected in every possible way.





